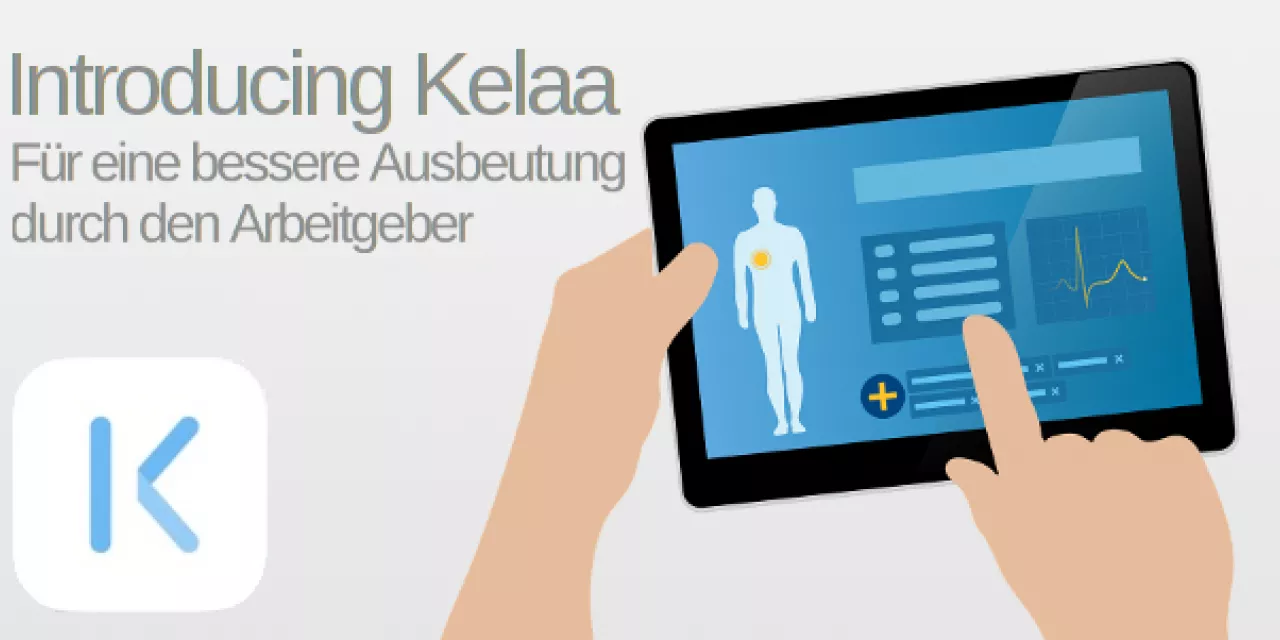
The BigBrotherAward 2018 in the “Communications” Category goes to Precire Technologies GmbH in Aachen for their scientifically dubious, probably illegal, and dangerous speech analysis.
Precire — Never heard of them? Maybe. But it is quite possible that Precire has heard from you.
Imagine you just applied for a new job. And — yay! — you have taken the first hurdle: you are invited for an interview. However, it’s going to be over the phone.
“Please describe your typical Sunday.”
Weird. That’s not exactly the question you expected at the beginning of a job interview.
“How was your last vacation?”
Your question “why are you interested in that?” is useless. Because this telephone interview is conducted by a computer in the first place, and secondly, it is not interested in you at all, and thirdly, even the company behind this phone-based job test is not interested in the content of your answers either. The computer on the phone simply wants a sample of your speech. And that means it needs to keep you talking about anything for 15 minutes.
“What do you enjoy most about your current occupation or your learned trade?”
Erm, interacting with people? Just kidding. But as we said, it’s not about what you say, but about how you say it. Precire, the company to whose telephone voice you are talking, claims that every person’s voice is as unique as their DNA. Precire also claims that they can derive a person’s character from a 15-minute speech sample, and figure out how suited they are for a certain job.
To that end, Precire allegedly decomposes recorded speech samples into over 500 000 components and analyses everything imaginable: pitch, volume, modulation, speed and rhythm. In addition it analyses the frequency of certain words, lengths of sentences, lengths of pauses, how convoluted the sentences are, how many filler words are used, how often words like “I” and the neutral pronoun “one” appear, how much variation there is in the voice, and also the acoustics. The computer also immediately assesses the speech as emotional or rational, cautious or forthright. To achieve this, Precire compares patterns it has found to those of test persons in its database. Precire then quickly applies to you the results of psycho-tests of persons who sound similar — and deduces your character from that.
The results are ratings such as those for freelance journalist Eva Wolfangel, who tested Precire on herself: she was found to be extremely curious (8 out of 9), but luckily was also very agreeable (also 8), sociable (7) and ready to take risks (6). At the same time the system judged that she had a “reserved style of communicating” and that she was “not very supportive”.1
First one thing, then another, on the one hand, and on the other hand. It sounds like the weekly horoscope on a crossword puzzle. Here is a example of such a horoscope:
“You wish for your fellow humans to like you, but still have a tendency to criticise yourself.” Or “Sometimes you seriously doubt that you have taken the right decision.” And a real gem: “You are intelligent and not easily fooled.”
Texts like these are trivial and the wording is somewhat flattering, but also slightly critical. There is always something that applies to everybody. Many people are taken in by that and think, “there’s really something to it!” The scientific term for this phenomenon is “Barnum effect”, named after the big circus.2
Precire, though, claims that their method is scientifically valid.3 They point to a book published by Springer Gabler, an academic publisher focusing on economics.
Scientific?
But it would be wrong to portray this as reputable science, as Dr. Uwe Kanning, professor for business psychology at the University of Applied Sciences Osnabrück critically explains in his book review.4 There is no independent research on the topic, he argues, and the algorithm is just a black box, the vendor’s trade secret. The available studies have not gathered their own numbers, but are masters’ theses based on data provided by Precire. The publication of further studies has resolutely been denied, even upon request. This was also criticised by freelance journalist Bärbel Schwertfeger.5
To recap: There is no evidence for a direct relationship between speech parameters and job performance. And there is no evidence that predictions created on that basis have any validity concerning the future performance of job applicants.6
Precire’s speech analysis will usually not find causality, but mere correlation. These can be completely random. One might as well base the decision on someone’s astrological sign. Or on shoe size. It would then go like this: if the computer finds that the three previously most successful employees all had shoe size 10, then it would hereafter recommend only persons with size 10 for management staff.
Media reports on Precire have appeared since 2015, and with few exceptions7 their gist largely was, “Look at this fascinating technology we have today!” Sometimes there is a slight sense of creeps, but hardly any journalist asks really tough questions or demands access to the studies allegedly supporting the scientific validity of Precire’s methods, which have been kept under wraps.
And nobody pierces through their numerous contradictions: On the one hand Precire claims that psychological tests are inconclusive, because the test persons could sense the desired answers. But on the other hand, Precire uses a data pool of speech samples of thousands of test subjects, whose characters were evaluated using psychological tests. To put it another way: their algorithms try to mimic the results of psychological tests. And nobody inquires why on the one hand there is talk about “immutable speech DNA”, while on the other hand Precire offers a speech training app8. Personnel development through speech training is the second part of Precire’s business model. The supposed “DNA” does not seem to be so immutable after all.
Participation in such a speech analysis is voluntary. Applicants cannot be forced to submit to a computer-based telephone interview. This is also true after the entry into force in 2018 of the European General Data Protection Regulation (GDPR), particularly Article 7, Paragraph 4 (“freely given consent”). But hey, how freely will the consent be given when it is about getting a very desirable job?
So who is using Precire? Allegedly more than 100 companies in Germany. Some of them are known: the recruitment agency Randstad, the insurance companies HDI and Gothaer, the transport business giant Fraport, the Handelsblatt newspaper, consulting company KPMG, electricity supplier RWE, health insurance company DAK, the Accor Hotels group, IBM and the mobile communications provider Vodafone.
Why on earth are companies doing that?
Because it is modern, and because they believe that it will lower their burden. The burden of preselection, and also the burden of decision-making. Computers are fast, and there are numbers. Numbers are facts, and computers are objective. Or are they?
Objective?
Thomas Belker, previously a board member for human resources at the Talanx insurance company — Talanx is a Precire customer — is convinced of the efficiency. So convinced, in fact, that he changed jobs and became the new CEO of Precire by 1 May 2019. He thinks that the programme not only saves time and money, but is also more objective, and therefore, more fair. Quote: “The machine knows nothing about subconscious prejduce, to which every human is subject. It does not care if someone is a man or a woman, or what colour his skin is.”9
As Dirk Gratzel, Precire co-founder, puts it: “A machine is much less error-prone than a recruiter. ‘Objective’ is the only thing a machine can do.”10
This is a very naïve point of view. Computers cannot “understand” us. But we must not confuse this with neutrality. Computer programmes are also subject to prejudice, because they are programmed by humans. Humans, who take their own sets of values for granted and incorporate those in the software. Humans with certain questions, goals and motives. But above all, the software is trained with a selected reference group of persons, which then defines what is seen as “normal”, good or bad.
Precire also offers services for the analysis of qualified management personnel. Here is the theory: whoever sounds like a manager of a DAX (german stock market index) company, might qualify as manager. Speech samples from managers of 30 DAX-listed companies were used as a basis. Of course they did not partake in these telephone interview shenanigans. Instead, Precire simply used speeches of the board members published on Youtube as base material. This not only methodically dubious. In a witty commentary Professor for business psychology Uwe Kannings (University of Applied Scienes Osnabrück) writes: “This study’s strong side is its entertainment value.” 11
But whether or not this is scientific: if the method is actually going to be used for selection of management personnel, the consequences are severe. As can be seen in the Precire advertising clip: “You are looking for someone who fits in with your team”. The picture shows a man in a grey suit and a red tie, welcoming to the team — you guessed it — another man in a grey suit and a red tie.12
According to a 2019 study, there are more managers called Michael than there are female managers of any name. The same is true for Thomas, Andreas, Peter and Christian.13
More diversity in the boards of directors? This is certainly not how it is going to happen. Selection methods like this, based on similarity, will only lead to hiring “more of the same”. Only now it is dressed up in the guise of Artificial Intelligence.
It is clear when it concerns humans, that the “human factor” plays a role. Prejudice by algorithm is more dangerous. It cannot be recognised as long as we believe the fairy tale of the “objective computer”.
Precire is riding a trend of using speech analysis for exploring and classifying people, and of ascribing magical powers of judgement to “Artificial Intelligence”. There is an unwitting side-effect to this: The cleaning-up of prejudices in the “algorithmic washing-machine” discreetly makes them respectable again. “The computer made that selection. We have no idea why”.
Not all company CEOs can warm to the idea of selecting personnel by computer. Sebastian Saxe, IT board member of the Hamburg Port Authority, says: “I am fond of digitalisation. But if we were to preselect applicants by software, we would never get to see people with rough edges who in the end turn out to be a good fit for us.14
Thank you for this clear statement.
Call centre
Maybe so far your thoughts were, “what a disgusting technology. But I am not looking for a job, so I am not affected.” Well, your thoughts would be wrong, because we now come to the third part of Precire’s business model: using speech analysis in call centres.
So how does that work? Call centres apparently record calls, forward them to one of Precire’s servers and have them analysed there in real-time. Precire then offers suggestions to the call centre agent on how to proceed. It is as if there were a psychologist sitting in the call centre agent’s ear at all times, listening in and whispering advice on what to say or what to offer next. For example, the software supposedly notices whether a customer is so enraged that she wants to terminate the contract, or whether she only wants to get a discount. Precire touts:
“Complaints are raw unconscious, emotional speech, a unique data source and an excellent opportunity to intensify lasting customer relationships.”
“Using a direct IT connection Precire analyses incoming complaints, recognises psychological patterns (…) and points out indications and anomalies to the deciders.”
“All the while the system itself is learning — in the case of the next-best-action-advice — with every new user (“Artificial Intelligence”) and helps you turn your customers’ speech data into real added value.15
Here, too, Precire’s marketing-speak sounds exaggerated. But in contrast to the prediction of a person’s suitability for a job, it is actually possible that speech analysis will find out something about the caller, such as someone’s origin via their dialect; emotions, insecurity, stress.
Since 2014 Precire has been advertising its services to call centres. Fittingly, the company became a member of the call centre association and of the German dialogue marketing association in 2016.16 It is however curiously reserved about providing tangible information about German call centres using speech analysis on callers. A quote by Precire founder Dirk Gratzel gives some insight into the possibilities: “We have an answer for everything desired by our customers.” For example: “What can the customer’s speech tell us about him?”, “Is this health-insured person depressed?”, “Is this client lying when filing his claim report?”17
This use of speech analysis in a call centre is not only unethical, it is illegal: it violates the confidentiality of telecommunications and the confidentiality of the spoken word (German criminal code: Strafgesetzbuch, “StGB”, Para. 201). This is a crime with substantial penalties.
It is high time for someone to rise up and open a criminal case. For example the data protection commissioner of the State of North Rhine-Westphalia. And the appropriate regulatory authorities should also take a very close look at Precire’s competitors, namely the start-ups “100 Worte” (“100 Words”) from Heilbronn and “Audeering” from Munich.
Detecting emotions and motivations via speech analysis is dangerous, because it can take place without our knowledge, hidden in the background, whenever we speak. This kind of speech analysis is perfectly suited for taking advantage of us. Individual people will lose more and more power, and unassailable power is getting concentrated at large corporations, insurance companies, banks and government authorities, who have access to our data and to these kinds of technologies.
We therefore call on the legislator: The use of speech analysis and “Artificial Intelligence” for the purposes of assessing personalities, emotions and motivations must be prohibited.
Dear listeners, the next time you are on the phone with a call centre and you hear the announcement that “parts of this call will be recorded for quality improvement”, state decisively at the outset: “No!” and “I do not want you to record this call!”
Learn to say “No”. With a friendly, but clear voice.
We say “No” to Precire.
Congratulations for receiving the BigBrotherAward 2019!
Laudator.in

1 Source: Riffreporter, Eva Wolfangel: "Google, wird meine Ehe halten?" (Google, will my marriage survive?) (Web-Archive-Link)
2 Barnum effect / Forer effect (Web-Archive-Link)
3 Precire website (translated): “Precire’s scientific basis is at the heart of the technology: numerous validation studies (internal and external) safeguard the process.” Original: “Die wissenschaftliche Fundierung von Precire ist das Kernstück der Technologie: Zahlreiche Validierungsstudien (intern, extern) sichern das Verfahren ab.” Quoted in Wirtschaftspsychologie aktuell, 6 Nov 2017: Ärger des Monats – Algorithmische Verirrungen (annoyance of the month: algorithmic aberrations) [Content no longer available]
4 Uwe P. Kanning: Sprachanalyse: eine neue Methode der Personalauswahl? (Speech analysis: a new method of selecting personnel?) (Web-Archive-Link)
5 Personalmagazin, 12/2015. By Bärbel Schwertfeger: Personalauswahl per Sprachtest. (Selecting personnel via speech test.) (PDF)
Comment by Bärbel Schwertfeger (Web-Archive-Link) below (translated): “Hi, as the author of the Personalmagazin article I have looked at Precire in detail and was left speechless several times about how they tried to ‘convince me’ and would never divulge any relevant data (a scientist who took an interest was even asked to sign a gagging contract) – including a cease and desist letter from a lawyer clearly intended to intimidate BEFORE the article appeared (nothing happened afterwards). A strange business strategy at least! But at least my test results earned me some great laughs from people who know me well. Bärber Schwertfeger” Original: “Hallo, als Autorin des Artikels im Personalmagazin habe ich mich ausführlich mit Precire beschäftigt und war doch mehrmals sprachlos, wie man versucht hat, mich “zu überzeugen” und partout keine relevanten Daten herausrückte (Ein Wissenschaftler, der sich dafür interessierte, sollte sogar einen Knebelvertrag unterschreiben) – einschließlich einer wohl als Einschüchterung gedachten anwaltlichen Abmahnung VOR Erscheinen des Artikels (danach kam nichts). Zumindest ein seltsames Geschäftsgebaren! Aber immerhin ernte ich mit meinem Testergebnis schöne Lacherfolge bei Menschen, die mich gut kennen. Bärbel Schwertfeger”
6 wirtschaftspsychologie-aktuell.de: Psychologische Diagnostik durch Sprachanalyse [Inhalt nicht mehr verfügbar]
7 Exceptions e.g. Bärbel Schwertfeger in Personalmagazin, 12/2015: Personalauswahl per Sprachtest. (Selecting personnel via speech test.) (PDF)
Eva Wolfangel at Riffreporter: "Google, wird meine Ehe halten?" (Google, will my marriage survive?) (Web-Archive-Link)
8 Precire-Coach described on the website (translated): “How we speak matters: As a coaching App, Precire helps to analyse your language and train your expression skills.” Original: “Wie wir sprechen, zählt: Als Coaching-App hilft PRECIRE, die eigene Sprache zu analysieren und das Ausdrucksvermögen zu trainieren.” [Content no longer available]
9 Source: Frankfurter Rundschau, 26 May 2018 Künstliche Intelligenz – Vorstand von Computers Gnaden. (AI – Leadership Position by the Grace of the Computer.) By Annika Leister. (Web-Archive-Link)
10 Source: Spiegel Nr. 3, 12 Jan 2019. By Martin U. Müller: Plaudernd zum Job (Chatting towards your job)
11 Source: Wirtschaftspsychologie-aktuell.de, 25 Apr 2018: Fachbuch im Fokus. By Prof. Dr. Uwe Peter Kanning. Book review of Klaus P. Stulle (Ed.): Psychologische Diagnostik durch Sprachanalyse. Validierung der Precire-Technologie für die Personalarbeit. Wiesbaden: SpringerGabler 2018 [Content no longer available]
12 Precire commercial video [Video no longer available]
13 Source: Manager Magazin, 6 Mar 2015, Analyse zur Frauenquote – Weniger Frauen in Vorständen als Männer, die Thomas heißen. By Christoph Rottwilm. (Web-Archive-Link) and Gründerszene: Michaels, Thomasse und Andreasse dominieren die Gründerszene. (Web-Archive-Link)
14 Source: Computerwoche, 16 Jun 2016: Personalauswahl 4.0 – Wenn Software in die Seele des Bewerbers schaut. (Personnel selection 4.0 – When Software looks into the Candidate’s Soul) By Michael Schweizer. (Web-Archive-Link)
15 These quotes were taken from Precire’s old website, today they can only be found with the Wayback Maching at archive.org. Back then Precire was called “Psyware” and used much more outright language. In 2016 the company changed its name – maybe the similarity to the word “spyware” was too sensitive to them after all … (Web-Archive-Link)
16 News on the Precire website, 22 Jul 2016: membership of the call centre association and of the German dialogue marketing association. [Content no longer available] (Web-Archive-Link)
17 Source: FAZ, 20 May 2015: Persönlichkeitsanalyse – Deine Sprache verrät dich. (Personality analysis – your language betrays you.) By Katrin Hummel. (Web-Archive-Link)